Security in depth
PHY018
Design a multi-layered system of security measures to increase protection.
Layering your physical security measures means the security of your people, information, and assets is not significantly reduced with the loss or breach of any single layer. By designing security measures that combine to support and complement each other, you will make it difficult for an external intruder or an employee to gain unauthorised access. This method is called ‘security in depth’.
To ensure security in depth, your organisation must:
- use a combination of measures to protect and control access to your people, information, physical assets, and premises
- select physical security products that provide the right levels of protection (as determined by your risk assessment).
Achieving security in depth
To achieve security in depth, layer the zones, working in from Zone 1 and increasing the protection with each new zone.
The following diagram shows a possible combination of security zones to achieve security in depth.
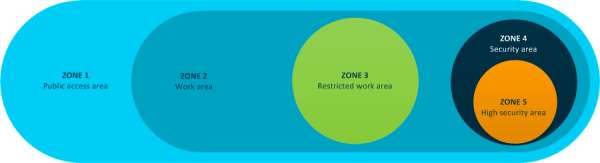
Because the security levels increase in line with the zones, you will be creating longer delays with each new layer you add. The cumulative delay gives you more time to respond to any attempts at unauthorised entry to the inner zones.
The following diagram shows how security in depth can provide enough delay for an effective security response.
Security incident timeline
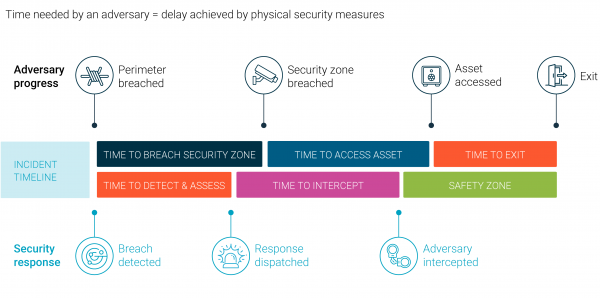
As the zone levels increase, your protective security measures should progressively change to protect information and physical assets.
The number of zones you need depends on the different levels of assurance and segregation required.
Sometimes, it isn’t possible for higher zones to be located fully within lower zones. In those cases, consider strengthening the external walls of the higher zones.
Zone 1 should include perimeter protection measures. For example, blast mitigation, counter-terrorism protection and so on.
You should work out the minimum and maximum zones required in your facilities. For example, organisations with:
- BILs of low to medium may only need zone 1 or zone 2
- BILs up to, and including, high to very high may need zone 1 and zone 2
- BILs up to, and including, extreme may need zones 1 to 4*
- BILs up to, and including, catastrophic may need zones 1 to 5**
* Use zones 3 or 4 for all general staff access areas rather than zone 2.
**Use zone 4 for all general staff access.
For more on the BILs, go to Applying the Business Impact Levels.
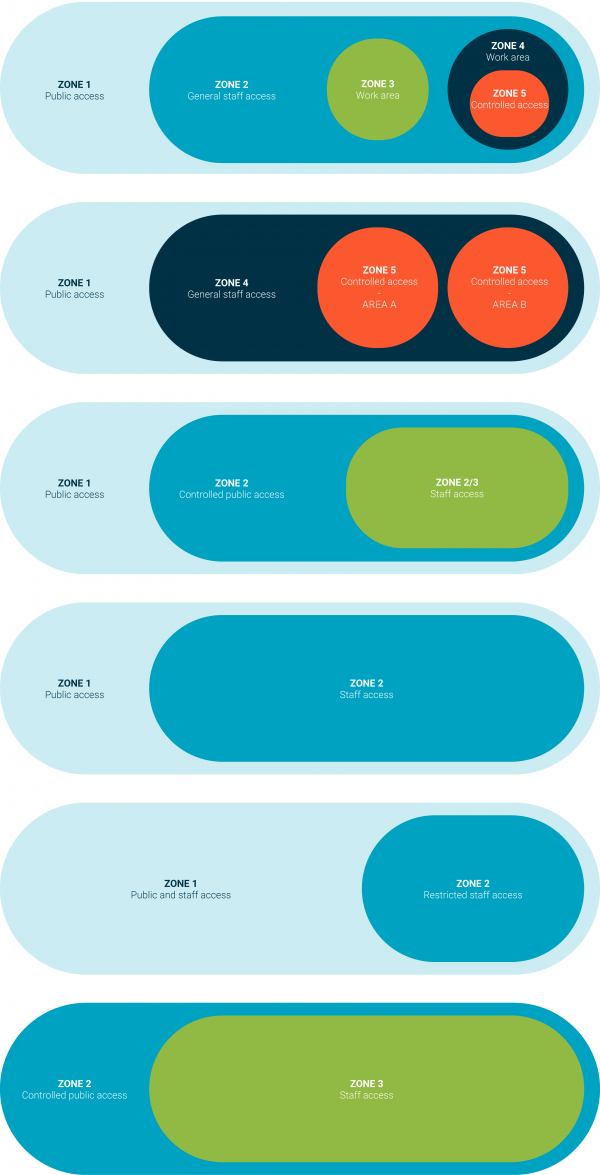
Diagram 3 shows some of the different ways that you can layer zones to provide increased protection.
Combining security zones to increase protection
Securing protectively-marked information and assets in security zones
Your organisation must comply with the minimum security requirements for protectively-marked information and assets.
Zones 3 to 5
Refer to the requirements set out in Table 1: Security zone requirements to protect marked information and assets with a BIL of extreme or catastrophic to national security.
You must also comply with ‘NZSIS Technical Note - Physical Security of Zone 5 Areas’ when constructing security areas to store TOP SECRET information or aggregated information with a catastrophic BIL. The information in the technical note is classified.
If for any reason your organisation can’t meet these requirements, you must get approval for each site from the originator of the material to hold any TOP SECRET information or aggregation of information with a catastrophic BIL.
When you’re constructing zone 3 or 4 areas that will store protectively-marked information, you must comply with ‘NZSIS Technical Note - Physical Security of Secure Areas’. This information is classified.


