INF003
When your information security controls are well designed and implemented, you reduce the risks of your information being compromised.
Encourage a strong security culture, so your information security practices are known and followed.
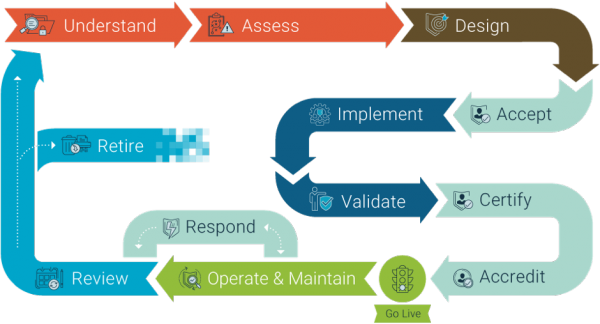
This protocol explains the steps your organisation should take to improve your information security. It sets out a lifecycle for managing information security, and outlines the mandatory requirements for New Zealand Government agencies.
Understanding the information security lifecycle and meeting the mandatory requirements will help you protect your organisation’s information. Read this protocol if you’re a:
- chief executive, chief security officer (CSO), or chief information security officer (CISO)
- senior manager responsible for information security, manager responsible for information management, senior manager, or line manager.
These principles should be read along with the Management protocol for personnel security, the Management protocol for physical security, and governance guidance for protective security.
As part of good practice, we recommend that private sector organisations also adopt the mandatory requirements for information security.
What is information security?
Information is an asset and information security is the protection you apply to keep your information assets secured from harm. Think of information in the broadest sense, not just in terms of information technology. Information exists in many forms (for example, electronic, printed, or spoken) and may reside inside or outside your organisation, including with your providers and clients, and in the cloud.
Information security is a broad concept that also includes cyber-security, digital security, and ICT security.